
The examples are everywhere: In November, wereported that malware was used to steal information about one of Japan's newest rockets and upload it to computers controlled by hackers. Critical systems attwo US power plants were recently found infected with malware spread by USB drives. Malware known as "Dexter" stole credit card data from point-of-sale terminals at businesses. And espionage-motivated computer threats are getting more sophisticated and versatile all the time.Some say we're living in a "post-PC" world, but malware on PCs is still a major problem for home computer users and businesses.
In this second installment in the Ars Guide to Online Security, we'll cover the basics for those who may not be familiar with the different types of malware that can affect computers. The malware comes in a variety of types, including viruses, worms, and Trojans.
Viruses are programs that can replicate themselves in order to spread from computer to computer, while targeting each PC by deleting data or stealing information. They can also change the computer's behavior in some way.
"Almost all viruses are attached to an executable file, which means the virus may exist on a system but will not be active or able to spread until a user runs or opens the malicious host file or program,"Cisco notes. "When the host code is executed, the viral code is executed as well. Normally, the host program keeps functioning after it is infected by the virus. However, some viruses overwrite other programs with copies of themselves, which destroys the host program altogether. Viruses spread when the software or document they are attached to is transferred from one computer to another using the network, a disk, file sharing, or infected e-mail attachments."
Worms are similar to viruses in that they replicate themselves to spread from machine to machine. Cisco says the main difference is a "worm operates more or less independently of other files, whereas a virus depends on a host program to spread itself." Worms spread easily and are likely to cause harm not just to individual PCs but to entire computer networks. One of the most destructive worms ever unleashed on the Internet was dubbed Slammer, which recently marked its 10-year anniversary.
Trojans do not replicate themselves, unlike viruses and worms. They are named after the Trojan horse of ancient Troy because they disguise themselves as legitimate, harmless programs to convince users to install them. "After it is activated, it can achieve any number of attacks on the host, from irritating the user (popping up windows or changing desktops) to damaging the host (deleting files, stealing data, or activating and spreading other malware, such as viruses)," Cisco writes. "Trojans are also known to create back doors to give malicious users access to the system."
Certain types of attacks combine attributes of viruses, worms, and Trojans into "blended threats" that may spread more effectively and be harder to defend against.
In addition to viruses, worms, and Trojans, malware can be divided further into sub-categories such as backdoors, remote access Trojans, information stealers, and ransomware. In his 2012 book "Malware, Rootkits & Botnets: A Beginner's Guide," Security expert Christopher Elisan describes these types of malware:
Backdoors
As their name implies, backdoors let hackers gain sneak attack access to an infected system, bypassing security "through the use of undocumented OS and network functions," Elisan writes. As an example, a backdoor was used to hack into RSA's systems in 2011. This was a targeted attack, gaining a foothold in RSA's network by sending innocent-looking phishing e-mails to workers. The e-mail had a subject line of "2011 Recruitment Plan" and contained an Excel file with an embedded Adobe Flash file that installed the backdoor:
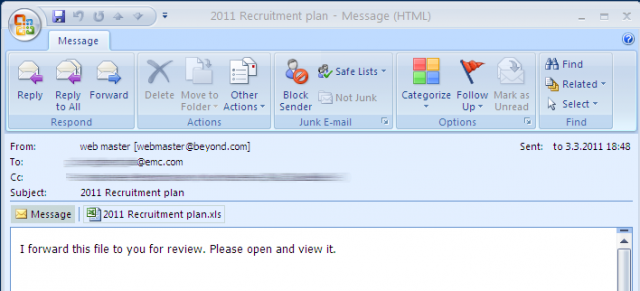 Looks legit, right?
Looks legit, right?
Launching the attachment in Outlook led to the Flash object being executed by Microsoft Excel. By targeting a vulnerability allowing the execution of code, the object dropped a variant of the so-called "Poison Ivy" backdoor onto the RSA computer. Poison Ivy connects back to servers operated by malicious users. "Once the connection is made, the attacker has full remote access to the infected workstation," F-Secure wrote in 2011. "Even worse, it has full access to network drives that the user can access."
Remote Access Trojans
"A remote access Trojan (RAT) is a malicious administrative tool that has backdoor capabilities, enabling an attacker to gain root access to the compromised machine," Elisan writes. "The main difference between a RAT and a traditional backdoor is that the RAT has a user interface, the client component, which the attacker can use to issue commands to the server component residing in the compromised machine."
Thousands of compromised computers can be controlled with remote access Trojans, letting attackers do "almost anything" they want. They can install programs on the infected PC, steal information, or just flat-out destroy the computer.
Information stealers
Diving deeper into malware designed to steal information, Elisan describes keyloggers, desktop recorders, and memory scrapers, which can steal passwords, financial credentials, proprietary data, "or anything that the attackers can use to their advantage or monetize."
A keylogger records the user's keystrokes and "stores them locally for later retrieval, or sends them to a remote server that the attacker has access to." Desktop recorders take periodic screenshots of the desktop, while memory scrapers take information out of a computer's memory while it's being processed. "Data that is processed in memory is unencrypted. This is why this is the best place to grab data," Elisan writes.
Keyloggers can be used for supposedly legitimate purposes, with some companies selling software letting you track the computer activity of family members. This might appeal to parents who want to monitor their children's Internet activity—or to someone who wants to spy on a cheating spouse.
Ransomware
 |
| A typical message displayed on a computer infected by ransomware. |
This type of malicious program essentially holds a computer hostage unless the user pays a ransom. The malware might encrypt the PC's data to prevent the user from accessing it. "To have access restored, the user needs to pay a ransom, after which the data will be decrypted by the malware or the user will be provided with a decryption tool and key," Elisan writes. "Or the criminal can just take the money and not bother anymore, leaving the user with the encrypted data and a hole in his pocket."
Similar ends can also be accomplished by locking the user out of the whole system or threatening destruction of the machine with a Trojan.
Ransomware builds on the annoying tradition of viruses bombarding users with popup ads for fake antivirus products. "Ransomware can be considered the successor of fake antivirus malware as the leading cybercrime threat facing consumers," Trend Micro wrote in a report recapping security in 2012. "Both threats cause users to worry about something (i.e., losing important data or downloading malicious files) and asks them to pay up to make the 'problem' go away."
Malware's spread
Malware isn't always detectable by users. In fact, the best malware can be impossible to detect without the use of advanced scanning programs or forensic software. That said, here are some telltale signs that your PC may be infected:
- Lots of popup messages, especially ones advertising antivirus software (these are fake!)
- Weird behavior in your Web browser, such as pages that refuse to close
- The home page or default search in your browser changes, or new toolbars are installed
- Programs start up for seemingly no reason
- Your computer freezes for a long time or is suddenly much slower than usual
- Files and folders are deleted or changed
- You get a ton of system error messages
- Your firewall tells you programs you're not aware of are trying to connect to the Internet
(For some tips on how to avoid malware and fix an infected PC, check out Microsoft's recommendations and see our previous article: "Yes, that PC cleanup app you saw on TV at 3am is a scam.")
Malware targets vulnerabilities in various types of applications or in the operating system itself, but more commonly it is propagated through browsers. This next chart from Microsoft's Security Intelligence Report shows that HTML and JavaScript, the markup and programming languages that power much of the Web, are the most common avenues to infect computers. In second place is Java, which has faced widespread attacks in browsers through Java plugins:
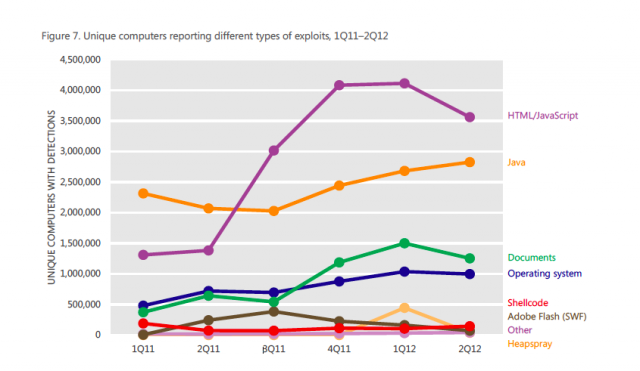 Microsoft Security Intelligence Report Volume 13
Microsoft Security Intelligence Report Volume 13
Malware can infect machines with almost no action by the user. For example, simply visiting a malicious website or a legitimate website that has been infected by hackers can sometimes be enough to infect the user's computer. So-called "drive-by downloads" infect PCs when a user goes to a malicious webpage that exploits vulnerabilities in a browser or plugin. (Software makers usually release updates that patch the vulnerabilities in the weeks or months after the bugs come to light, creating a cat-and-mouse game between developers of legitimate programs and malware purveyors.) Lots of malware still requires some action by the user, however, like clicking a spam e-mail attachment or downloading an infected file from the Internet.
Windows security has improved greatly in recent releases such as Vista, Windows 7, and Windows 8, with features like User Account Control to prevent applications from installing without user consent. Defenses such as address space layout randomization and data execution prevention have also made it much harder for attackers to exploit vulnerabilities in a way that allows malicious code to be installed on a system. But vulnerabilities in other software, such as Java, have been increasing. Apple's Mac computers, long seen as safe havens because of their low market share, have also become a bigger target.
"It is impossible to completely prevent vulnerabilities from being introduced during the development of large-scale software projects," Microsoft noted in its most recent Security Response Center Progress Report. "As long as human beings write software code, no software will be perfect and mistakes that lead to imperfections in software will be made."
Even security products aren't immune, as we saw with the revelation that firewall, VPN, and spam filtering gear sold by Barracuda Networks contained backdoors that let attackers remotely log in and access sensitive information.
Malware is often able to escape detection by using rootkits, which allow privileged access to critical parts of the system and can hide a program's existence. A rootkit, as we noted in a previous article, is "software that tampers with operating systems at a low level to evade detection." A rootkit isn't automatically malware but is technology used by malware to achieve its ends in secret. Rootkits can "hide the presence of particular processes, folders, files and registry keys," Kaspersky Lab notes.
Besides attacking infected computers, one major use of malware is to create botnets—giant networks of "zombie" computers that can be made to carry out a variety of nefarious actions.
A computer that has been joined to a botnet may not harm its owner directly. Instead, the infected PCs in the botnet go on the offensive, carrying out commands issued from a server controlled by a criminal.
"A bot agent can be a stand-alone malware component in the form of an executable or a dynamic link library (DLL) file or a piece of code added to the malware code," Elisan writes. "The bot agent’s main function is to establish communication with the botnet’s network component."
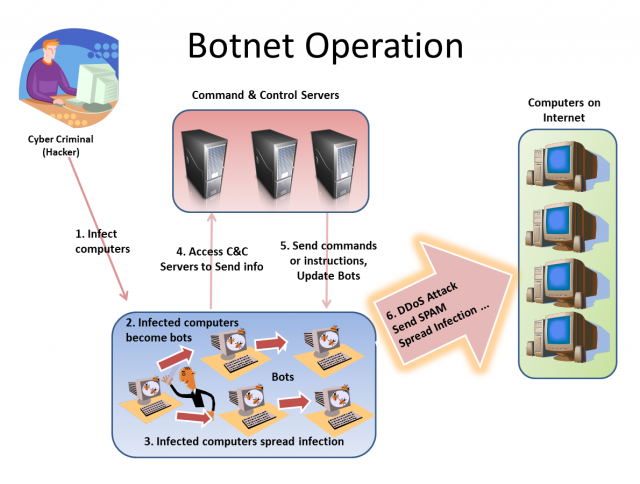
Botnet basics
Botnets can be used for many nefarious purposes, including distributed denial-of-service attacks, which send extraordinary amounts of traffic to a website in order to cripple it. Botnets can be used for click fraud, in which thousands of computers click ads to generate revenue for criminals. A single botnet can perform numerous attacks. In fact, many criminals who run botnets simply rent out accessto the infected PCs to other criminals who find ways to monetize them.
Botnets also send out much of the world's spam e-mail. The so-called Rustock botnet was responsible for about 60 percent of the world's spam at its peak in August 2010, but it was taken offline by a sophisticated operation early in 2011.
Businesses under attack
Businesses end up suffering from malware in all sorts of ways. A bank or credit card company might lose money when customers' PCs are infected, as the companies often reimburse the customers for lost funds. Websites, as noted above, can be hit with denial-of-service attacks from botnets. Or malware can run rampant through a company's offices upon gaining a foothold on even just one PC.
Banks and other financial organizations have long been targeted by malware that modifies banking websites to get into user accounts. Banks have adopted stricter security measures to prevent accounts from being hacked, but attackers have upped their game with more sophisticated automatic transfer systems (ATS).
In 2012, "ATSs became a key threat facing smaller businesses," Trend Micro wrote in its annual security report. "ATSs remove middlemen, usually a keylogger or a WebInject file, when siphoning funds. Instead of passively stealing information, ATSs automatically transfer funds from the victims’ to the cybercriminals’ accounts. This makes fraud more difficult to detect on the part of banks, as the transaction appears to be made by the user and not a potentially fraudulent third party. By contrast, traditional banking malware require human intervention to transfer funds, which is a slower process and may easily be detected by banks."
Various data breaches and attacks targeting specific businesses continued apace in 2012, Trend Micro noted. Often, attacks against businesses start by exploiting a single weak link.
"Generally, malware outbreaks start slowly," McAfee writes in a case study. "The first device to get infected is often a workstation or laptop that does not have adequate defenses. Anti-virus software is not installed, not current, or disabled. The operating system and applications are not patched. Sometimes a user inadvertently puts themselves, and company assets, at risk by installing browser plug-ins, cruising questionable websites, or clicking on suspicious links in e-mail messages."
That's as good a reason as any to keep your PC up to date with all the latest security fixes—and cast a suspicious eye toward sketchy-looking e-mails and websites.
They need to protect the equipment, files, and even the cash they store in the workplace.
ReplyDeleteWith Lock Service you can get your lock barrels changed, lock cylinders replaced to suit your keys.
While replacing locks it might be a good time to consider something other than the standard deadbolt
lock that is usually on entry doors.
Also visit my site: locksmith school